Microsoft has unveiled its Asia Pacific findings from the latest edition of its Security Endpoint Threat Report 2019, which revealed a decrease in cyberthreat encounters in Malaysia, across cryptocurrency mining, malware and ransomware encounters and drive-by download attacks, in the last year.
Findings were derived from an analysis of diverse Microsoft data sources, including 8 trillion threat signals received and analysed by Microsoft every day, covering a 12-month period, from January to December 2019.
“As security defenses evolve and attackers rely on new techniques, Microsoft’s unique access to billions of threat signals every day enables us to gather data and insights to inform our response to cyberattacks,” said Mary Jo Schrade, assistant general counsel, Microsoft Digital Crimes Unit, Microsoft Asia.
“The Microsoft Security Endpoint Threat report aims to create a better understanding of the evolving threat landscape and help organisations improve their cybersecurity posture by mitigating the effects of increasingly sophisticated attacks.”
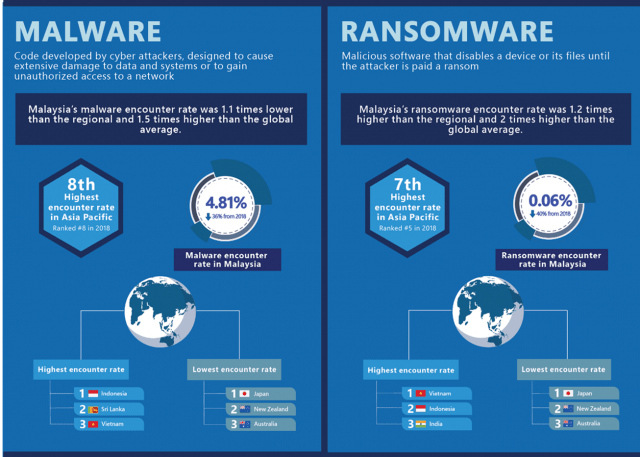
According to the report, Asia Pacific continues to experience a higher-than-average encounter rate for malware and ransomware attacks – 1.6 and 1.7 times higher than the rest of the world, respectively.
Malaysia’s malware encounter rate decreased by 36 percent and stood at 4.81 percent. This was the 8th highest encounter rate across the region, and 1.1 times lower than the regional average.
Ransomware encounters decreased by 40 percent and stood at 0.06 percent. This was the 7th highest encounter rate, across the region, and 1.2 times higher than the regional average.
“Despite a reduction in the number of encounters, cyberattacks remain a serious threat to organisations across Malaysia,” said Haji Amirudin Bin Abdul Wahab, Chief Executive Officer of CyberSecurity Malaysia.
“With the announcement of the Movement Control Order (MCO) in March, we saw a shift to remote working, leveraging technology to sustain business continuity. This shift simultaneously demands attention to cybersecurity, which many organisations have taken very seriously. The Security Endpoint Threat report findings provide valuable insight and understanding for organisations to leverage as they continue to work in a digital environment moving forward.”
“Often, high malware encounters correlate with both piracy rates and overall cyber hygiene, that includes regular patching and updating of software. Countries that have higher piracy rates and lower cyber hygiene tend to be more severely impacted by cyberthreats. Patching, using legitimate software, and keeping it updated can decrease the likelihood of malware and ransomware infections,” explained Dzahar Mansor, National Technology Officer, Microsoft Malaysia.
During such attacks, victims’ computers are infected with cryptocurrency mining malware, allowing criminals to leverage the computing power of their computers without their knowledge. Malaysia recorded a 69 percent decrease in cryptocurrency mining encounter rate, from 0.16 in 2018 to 0.05 in 2019. This was the 7th highest encounter rate across the region, on par with both the regional and global average.
On the declining encounter rate recorded, Amirudin elaborated, “Cybercriminals are usually incentivised by quick financial gains. The recent fluctuations in the value of cryptocurrency and the increased time required to generate it has perhaps led to them focusing on other forms of cybercrime.”
The drive-by download attack volume[2] in Asia Pacific has converged with the rest of the world at 0.08, declining by 27 percent from 2018.
Malaysia experienced a significant decrease in drive-by download attack volume, by 93 percent, which stood at 0.04 in 2019. This was the 9th highest attack volume across the region, and 2 times lower than the regional and global average.
These attacks involve downloading malicious code onto an unsuspecting user’s computer when they visit a website or fill up a form. The malicious code that is downloaded is then used by an attacker to steal passwords or financial information.
Despite the general decline in drive-by download attacks across the region, the study found that regional business hubs, Singapore and Hong Kong, recorded the highest attack volume in 2019, over 3 times the regional and global average.
“We usually see cybercriminals launch such attacks to steal financial information or intellectual property. This is a likely reason why regional financial hubs recorded the highest volume of such threats. The high attack volume in these markets may not necessarily translate into a high infection rate, perhaps due to their good cyber hygiene practices and use of genuine software,” explained Dzahar.
“This means that attackers have been pivoting their existing infrastructure, like ransomware, phishing, and other malware delivery tools, to include COVID-19 keywords, to capitalize on people’s fear. Once users click on these malicious links, attackers can infiltrate networks, steal information and monetise their attacks,” he added.
Since the outbreak, Microsoft Intelligence Protection team’s data has shown that every country in the world has seen at least one Covid-19 themed attack, and the volume of successful attacks in outbreak-hit countries seems to be increasing, as fear and the desire for information grows.
Of the millions of targeted phishing messages seen globally each day, roughly 60,000 include Covid-19 related malicious attachments or malicious URLs. Attackers are impersonating established entities like the World Health Organization (WHO), Centers for Disease Control and Prevention (CDC), and the Department of Health to get into inboxes.
Microsoft further encouraged businesses to have strong tools to safeguard employees and infrastructure. This means looking into multi-layered defense systems and turning on multi-factor authentication (MFA) as employees work from home. Additionally, enable endpoint protection and protect against shadow IT and unsanctioned app usage with solutions like Microsoft Cloud App Security
They are also urged to ensure employee guidelines are communicated clearly to employees. This includes information on how to identify phishing attempts, distinguishing between official communications and suspicious messages that violate company policy, and where these can be reported internally and to also choose a trusted application for audio/video calling and file sharing that ensures end-to-end encryption